nslookup
Nslookup (stands for “Name Server Lookup”) is a useful command for getting information from DNS server. It is a network administration tool for querying the Domain Name System (DNS) to obtain domain name or IP address mapping or any other specific DNS record. It is also used to troubleshoot DNS related problems.
Syntax:
nslookup [option]
Options of nslookup command:
nslookup google.com:
nslookupfollowed by the domain name will display the “A Record” (IP Address) of the domain. Use this command to find the address record for a domain. It queries to domain name servers and get the details.

nslookup 192.168.0.10: Reverse DNS lookupYou can also do the reverse DNS look-up by providing the IP Address as argument to nslookup.

nslookup -type=any google.com: Lookup for any recordWe can also view all the available DNS records using -type=any option.

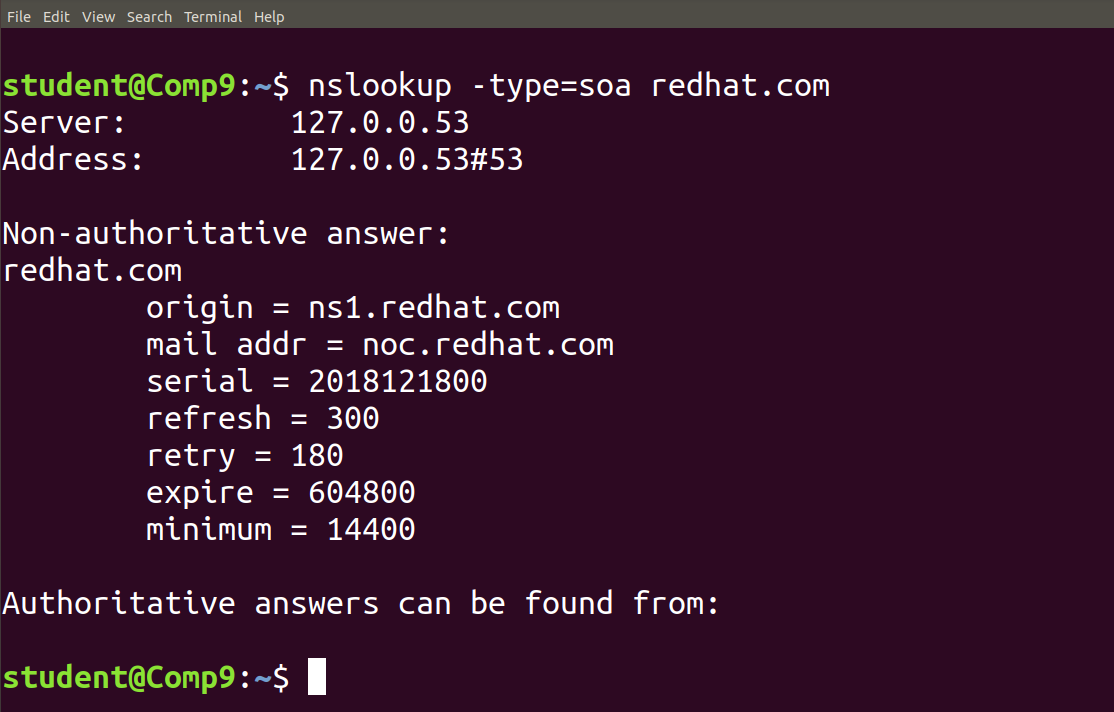
nslookup -type=soa redhat.com: Lookup for an soa recordSOA record (start of authority), provides the authoritative information about the domain, the e-mail address of the domain admin, the domain serial number, etc…
nslookup -type=ns google.com: Lookup for an ns recordNS (Name Server) record maps a domain name to a list of DNS servers authoritative for that domain. It will output the name serves which are associated with the given domain.

nslookup -type=a google.com: Lookup for an a recordWe can also view all the available DNS records for a particular record using -type=a option.

nslookup -type=mx google.com: Lookup for an mx recordMX (Mail Exchange) record maps a domain name to a list of mail exchange servers for that domain. The MX record tells that all the mails sent to “google.com” should be routed to the Mail server in that domain.

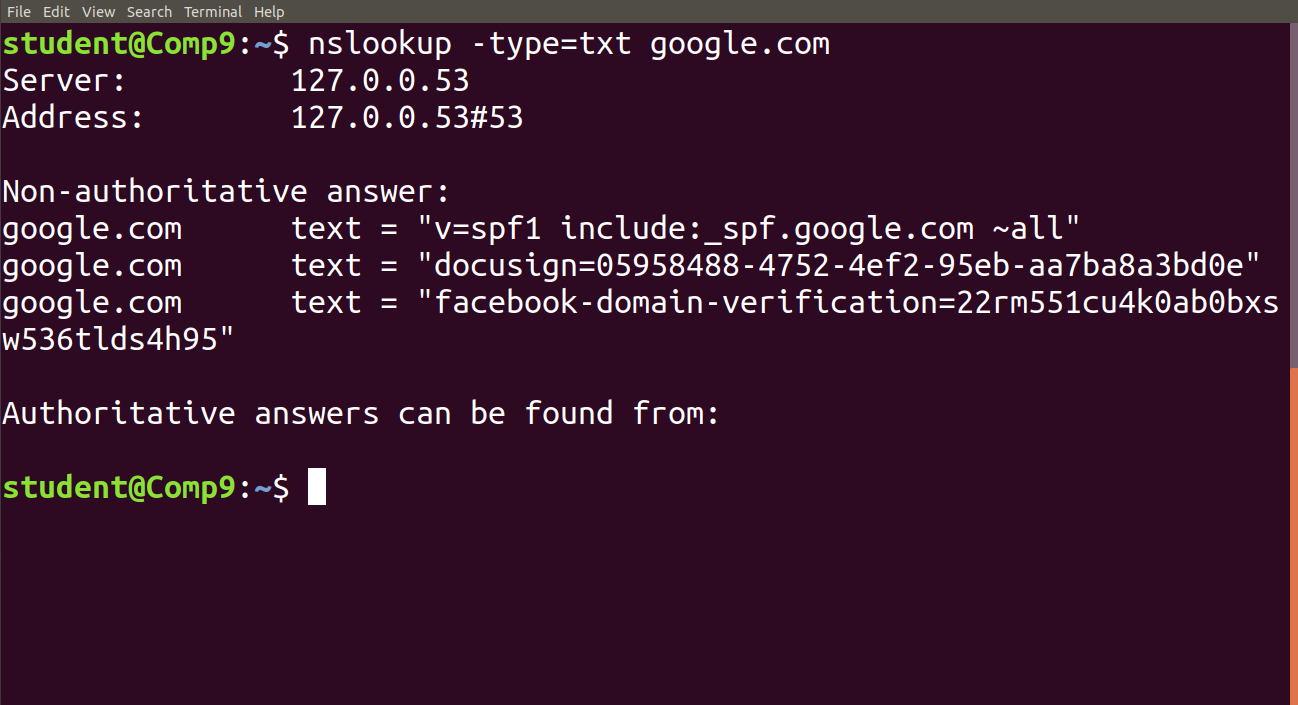
nslookup -type=txt google.com: Lookup for an txt recordTXT records are useful for multiple types of records like DKIM, SPF, etc. You can find all TXT records configured for any domain using below command.
Comments
Post a Comment